When we moved out of the rental and bought a house, I compiled a list. In anticipation of the chores to come, I knew I’d need a reminder as to why we left (and gave up free maintenance). One of the entries on this list pertained to the garden. A garden is a very personal project–it betrays much about its creator, being infinitely customizable. And it is because of this customization that no two people can agree on a garden’s layout.
But it’s a comparatively minor issue to have marital bickering over a layout. When the property is a rental, however, the owner, and by extension the management, gets final say. And often, they exercise this executive power by giving a hired landscaping company carte blanche, without ever consulting the tenants. My first experience with this involved the empty pot of dirt by the front door. Our unit shared the walkway to the model (the unit that’s way nicer than anything they rent out), so it was maintained better than the collapsing structures which comprised the rest of the compound. But for whatever reason, this pot sat unused. I let it remain this way for the entire first year.
On year two, however, it was impossible to overlook the eyesore, and I invoked eminent domain. Its location was on the south side of the building, upon concrete and brick–it was a hot and dry pot of dirt. I concluded that this would make an excellent herb garden. When early spring came the following year, I started seed in anticipation. After last frost, I topped the pot off with a good potting soil (the pot’s contents had long since compacted to a crusty and barren dust), and planted my seedlings.
The landscapers promptly came through, ripped out my herbs, and planted petunias. Enraged, I grabbed a bucket and retrieved from the pot the potting soil I had purchased, and re-used it in the back garden. The petunias, not only uprooted but now exposed to the unrelenting sun, and going without water because apparently management didn’t assign garden watering duties to anyone, withered and died, leaving a fallow vessel of dirt once again for the remainder of the year.
A couple years later, I had a similar non-verbal disagreement with the landscapers when I planted morning glories along the back fence. I constructed a zigzag trellis of fishing line so that the plants could make a pretty cover as they grew up the invisible wire. Then, as the plants were nearing the top, the landscapers reached over the fence and ripped out the plants, along with the fishing line. I stewed over this transgression for a long time thereafter.
For years I grew morning glories in a pot in the center of the patio–far away from the murderous hands of hired thugs. Then one year, I noticed that I started getting volunteers. I let them grow, and they turned out to be far more invasive than store-purchased seed. Ultimately I concluded that they had cross-pollinated with bindweed, as they bore similar characteristics. I dubbed these “Evil Morning Glories”, as their voracity rivaled kudzu.

Bitterly remembering the cruelty of prior years, when this batch of morning glories went to seed, I saved some. But this would turn out to be unnecessary, as once upon the earth, these plants would prove to be ruthless. The following year, they exploded upon the fence with unholy fervor. And despite their physical removal and chemical applications (once again at the hands of the landscapers), they could not be eradicated. This is my gift to the apartment complex–the ultimate landscaping nemesis, a reminder for all eternity!
 But when you dance with the devil…okay that’s a little dramatic. I took seed with me, and against better judgement, planted it at the house. Come spring, the devil’s progeny will once again plague the land, yet evil always accompanies beauty.
But when you dance with the devil…okay that’s a little dramatic. I took seed with me, and against better judgement, planted it at the house. Come spring, the devil’s progeny will once again plague the land, yet evil always accompanies beauty.
–Simon

 And all I was after was the sharing of knowledge and information, and to physically sit near each other. My request for a desk near the Operations team was immediately denied. Then, as the discussions began to involve higher levels of management, they died. Some of the changes were minor, like upgrading to HTML5, or implementing RSS update feeds. But ultimately, sensing stagnation and seeing opportunity elsewhere, I took a promotion and transferred to Marketing.
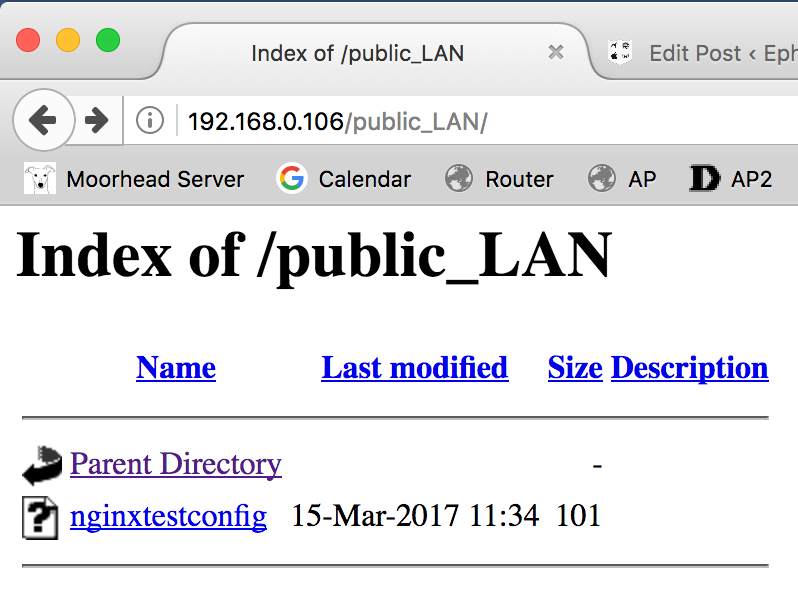
And all I was after was the sharing of knowledge and information, and to physically sit near each other. My request for a desk near the Operations team was immediately denied. Then, as the discussions began to involve higher levels of management, they died. Some of the changes were minor, like upgrading to HTML5, or implementing RSS update feeds. But ultimately, sensing stagnation and seeing opportunity elsewhere, I took a promotion and transferred to Marketing. Natrually I would never be caught dead using IIS, although I was forced to use it for a prior job. But my server, Linux-based of course, leverages NGINX with an Apache backend. I had a working familiarity of Apache, and I had already dabbled with .htaccess and .htpasswd files before, as well as modifying the Apache config files to allow their overrides, so this seemed like the best option.
Natrually I would never be caught dead using IIS, although I was forced to use it for a prior job. But my server, Linux-based of course, leverages NGINX with an Apache backend. I had a working familiarity of Apache, and I had already dabbled with .htaccess and .htpasswd files before, as well as modifying the Apache config files to allow their overrides, so this seemed like the best option.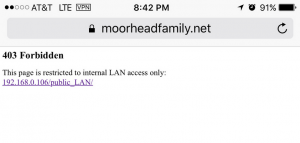
 Remember that story with the little people who would steal insignificant items from around the house in order to craft useful tools needed for their survival? It was a humorous take on the phenomenon of small and low-value clutter vanishing, seemingly without explanation. It’s an innocent way to cope with the irritations of their misplacement.
Remember that story with the little people who would steal insignificant items from around the house in order to craft useful tools needed for their survival? It was a humorous take on the phenomenon of small and low-value clutter vanishing, seemingly without explanation. It’s an innocent way to cope with the irritations of their misplacement.