That’s actually how a company higher-up referred to it: The Internets and Social Medias. I felt like a kid, talking to some adult who was desperately trying to understand “what the kids are into these days”. It was painful.
The point of that particular email communication was to be careful that when you take to the Internet to obnoxiously voice your opinion about something, as we are all apt to do, that you take pains to avoid having your opinion interpreted as a representative of your employer. Remember Chick-fil-A and that comment against homosexuals by whoever that executive was? I get that it’s a Christian company, but it seemed odd to me that we were holding a company accountable for an employee’s personal opinion. I don’t recall the company ever catching flak for refusing to hire homosexuals, or denying them service, so as far as I know, the company itself hadn’t done anything ethically questionable. But it demonstrated that people as a whole didn’t want to make that distinction, and so proved my own employer’s concerns.
My point is that this is one consequence of the Internet, which represents something greater: open access to exercise free speech to a worldwide audience, and the major consequences it can have against a powerful individual, whether or not those consequence are justified. It’s a definite point of concern, but it got me thinking about something even bigger: who specifically would be against this paradigm that we’re in a constant state of disagreement regarding the openness of the Internet?
And my conclusion is simply, that it’s those with the most to lose. Let’s consider some logic: knowledge is obtained through experience and study. Study is written information, vetted and discussed. The Internet is the biggest and most available source of vetted information. The internet is therefore knowledge incarnate. An argument against the openness of the internet, therefore, is an argument for greater widespread ignorance. So who would benefit? I surmise that it would be those who are in power. Why? Because the mere fact that they hold positions of power demonstrates that they have benefited from the existing system to this point, which compared to today’s access to information (courtesy of the Internet), has been a period of relative ignorance.
People fear to lose what they have acquired, even when recognizing it doesn’t benefit the common good. More tangibles means a higher standard of living–something for which we fight tirelessly–human nature. Conclusion: those in power don’t want to lose power, and consequently perceive the Internet as a direct threat to their power.
Enter: government intervention. The trend has been to cripple the Internet where its ubiquity benefits the commoner, without threatening areas in which it benefits commerce (AKA: the flow of money and by proxy, power). This translates to being able to monitor who does what on the Internet. If you can build a profile on every citizen, then through historically successful tactics of government action; such as intimidation, threats, political imprisonment; you can then silence anyone who’s informed enough to be a direct threat without destroying the technology itself, and therefore still capitalize upon it while maintaining the power dynamic.
The first approach was to damage the first threat to surveillance: encryption. In the 1990s there were actual laws which dictated the effectiveness of Internet encryption strength, and even went so far as to classify the technology as a munition, and therefore precluded from international export. Review the history of PGP for an amusing example.

But stifling encryption ultimately harmed commerce, as the Internet became increasingly commerce-centric. Money had to flow and it could only do so with encryption. The restrictions eased, but encryption remained cost-prohibitive to anything outside of commerce, so for a time the government was still in a winning position. More interested in communication and people’s access to information, the government was still comfortable with the fact that while strong encryption existed, nothing they were interested in monitoring was encrypted.
But then, encryption became universal, recently thanks in part to the push for it by companies such as Google, Mozilla, Apple, and the EFF. Suddenly, it became infeasible to police the public based on their Internet traffic. So the government responded with what they tried before: breaking encryption. Except this time, the commercial Internet entities were no longer solely comprised of companies who unquestionably took the government’s side in all matters. Encountering resistance by these powerful companies, attempts to renew similar legislation have so far failed (in the US, anyway–Brazil and Britain are two notable counterexamples).
So the power play has taken a new approach. If you can’t control the technology that runs the Internet, control the infrastructure itself. In order to do that, it needs to be consolidated–monopolized. Enter the era of mega-mergers.
Time Warner/Comcast/Charter/Verizon/Level 3/AOL–the Internet backbones of the country are quickly becoming one. In a closed-door tit-for-tat arrangement, these companies assuaged the government leaders’ fear, by providing all the financial incentive required to keep these leaders in power, while the leaders responded by further de-regulating legal restrictions, allowing these companies to squeeze additional capital from it’s customer base. But as stated, there’s a bigger plan. This mutually-beneficial arrangement extended to ignore antitrust regulations, giving companies the monopolistic power they wanted to maximize revenue from a competition-less industry, while becoming unofficially indebted to the government, true, but the government will then will exercise its power to regulate these indebted monopolies for its own purposes, finding away around the technology to access customer data through the gatekeepers themselves. And once the industry is monopolized, there will be no fringe competitors available to offer alternatives.
So what is the next step? I will theorize. Ultimately we’ll end up with one or two ISPs. We’ll pay increasingly exorbitant prices for Internet access. Then they’ll leverage their monopoly over the Internet backbone itself to force a technological loophole. ISPs may require that customers install an ISP-provided encryption certificate, which would break encryption to the ISPs while still maintaining secure communications for commercial purposes. They may require customers to use ISP equipment, designed for a similar middle-box proxy service. They may require something at their business customers’ end, such as logging and surrendering customer information. There are many specific possibilities, but what’s important is that we as the customer, with no other ISP alternative, will be in no position to refuse. And the pseudo-anonymity, open exchange of ideas, and access to the world’s repository of knowledge; will gradually be lost to the ages until the next violent revolution.
–Simon


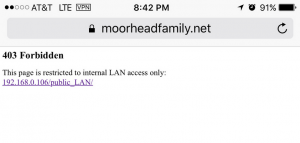
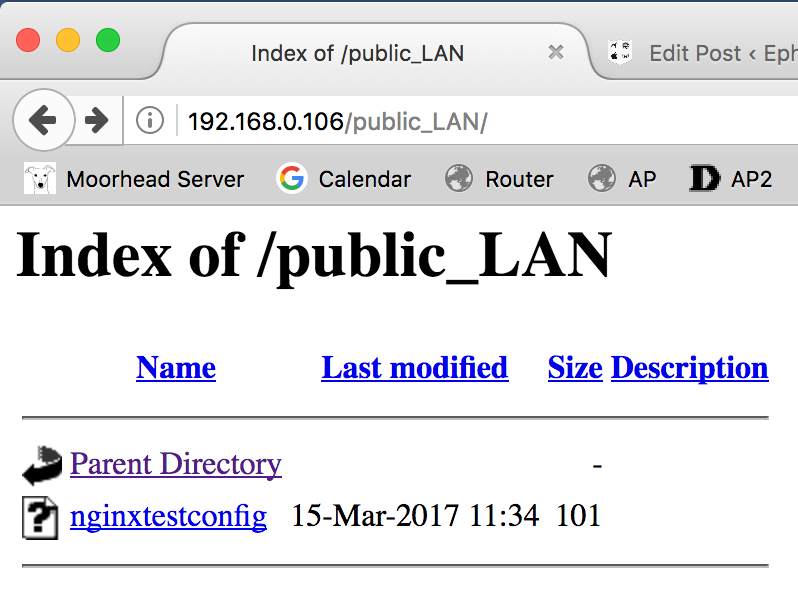
 In accordance with Lets Encrypt’s (the certificate authority for this site) 90-day SSL certificate expirations, I needed to renew the certificate for this site. It should be seamless, but if you are using any applications that support certificate pinning, you may receive a notice of a certificate mismatch. This is normal, and the alert serves as a warning against a possible certificate forgery. Simply accept the new certificate. However, for the extra paranoid (myself included), you may validate the new certificate’s authenticity with the below fingerprints:
In accordance with Lets Encrypt’s (the certificate authority for this site) 90-day SSL certificate expirations, I needed to renew the certificate for this site. It should be seamless, but if you are using any applications that support certificate pinning, you may receive a notice of a certificate mismatch. This is normal, and the alert serves as a warning against a possible certificate forgery. Simply accept the new certificate. However, for the extra paranoid (myself included), you may validate the new certificate’s authenticity with the below fingerprints: Natrually I would never be caught dead using IIS, although I was forced to use it for a prior job. But my server, Linux-based of course, leverages NGINX with an Apache backend. I had a working familiarity of Apache, and I had already dabbled with .htaccess and .htpasswd files before, as well as modifying the Apache config files to allow their overrides, so this seemed like the best option.
Natrually I would never be caught dead using IIS, although I was forced to use it for a prior job. But my server, Linux-based of course, leverages NGINX with an Apache backend. I had a working familiarity of Apache, and I had already dabbled with .htaccess and .htpasswd files before, as well as modifying the Apache config files to allow their overrides, so this seemed like the best option.